The Myth of Total Anonymity
The first cryptocurrency draws originated from its digital cash concept which provided users with complete anonymity and freedom. The complete anonymity of crypto transactions remains uncertain as we progress into 2025.
Is crypto really anonymous?
The pseudonymity of Bitcoin and Ethereum doesn’t mean, in any way, that they are absolutely anonymous. The blockchain system keeps an everlasting record of all transactions which enables full traceability of these transactions. The government uses blockchain analytics tools from Chainalysis and Elliptic to link digital wallets to actual individuals because of this openness.
The tracking ability demonstrates increasing privacy issues in digital finance because users face more monitoring when their transactions link to KYC-compliant exchanges. The article [cited] shows the wide surveillance systems governments have established which means crypto users must understand that complete anonymity does not exist and they need to understand tracking tools to protect their privacy.
How Governments Track Crypto Transactions?
The ways governments track crypto transactions are getting more advanced as digital currencies change. The open nature of blockchain technology enables law enforcement to track transactions through publicly accessible ledgers.
The tracking of cryptocurrency transactions becomes more efficient through the help of companies like Chainalysis and Elliptic which enable authorities to identify wallet owners by analysing their usage patterns. So, money connected to exchanges and accounts that follow Know Your Customer (KYC) rules can be traced pretty easily.
Blockchain transactions appear to be anonymous, but they do not provide complete privacy. The government tends to notice big transactions when they appear suspicious or when they are connected to suspicious activities.
Cryptocurrency transactions are eternally chronicled on blockchains, as formerly specified, which are public distributed ledgers, displaying how simply governments can trace activities.
Therefore, it’s imperative to comprehend how these tracking systems work if you intend to desire to use crypto and retain your privacy.
Government Crypto Tracking Tools Explained
![]()
Overview of India’s New Income Tax Bill and Financial Surveillance Measures
| Tracking Method | Description |
| Blockchain Analysis | Law enforcement agencies utilize blockchain analytics tools to trace cryptocurrency transactions, leveraging the transparent and immutable nature of public blockchains to identify illicit activities. These tools analyze transaction patterns and wallet addresses to uncover connections between individuals and transactions. |
| Regulatory Reporting Requirements | Governments impose reporting obligations on cryptocurrency exchanges and service providers to collect data on transactions, enhancing oversight and compliance with anti-money laundering (AML) and countering the financing of terrorism (CFT) regulations. This data collection aids in monitoring and investigating suspicious activities. |
| Collaboration with Financial Institutions | Authorities collaborate with banks and financial institutions to monitor cryptocurrency transactions, leveraging existing financial networks to detect and prevent illicit activities. This collaboration includes sharing information and coordinating efforts to track suspicious transactions. |
| Use of Privacy Coins | The emergence of privacy-focused cryptocurrencies, such as Monero, presents challenges for tracking transactions due to enhanced anonymity features. These coins employ technologies that obscure transaction details, making it more difficult for authorities to trace activities.
|
| International Cooperation | Governments engage in international cooperation to track cross-border cryptocurrency transactions, sharing information and coordinating efforts to combat global illicit activities. This cooperation includes working with international organizations and foreign law enforcement agencies. |
Government Tracking of Cryptocurrency Transactions
Can the Government See Your Crypto Wallet?
The digital era has generated privacy problems which force users to doubt government access to cryptocurrency wallets while users attempt to remain anonymous.
The transparent nature of blockchain transactions enables authorities to track funds because transactions are recorded on a public ledger when wallet addresses are linked to identifiable individuals through Know Your Customer (KYC) regulations enforced by exchanges.
Non-KYC wallets seem to protect user identity at first but large or repeated transactions can attract unwanted scrutiny which may signal governmental interest.
The difficulty of accessing crypto wallets directly does not stop governments from tracking users through IP address monitoring and blockchain transaction behaviour analysis to build comprehensive user profiles.
The ability to understand digital traces stands as a crucial element for people who want to protect their financial privacy while dealing with this difficult situation so they must develop methods to reduce surveillance risks.
How to Avoid Crypto Surveillance by Government?
While achieving complete anonymity in cryptocurrency transactions can be challenging, as most cryptocurrencies like
Bitcoin are pseudonymous relatively than verily anonymous; several methods and apparatuses can help augment your privacy:
Privacy-Focused Cryptocurrencies (Privacy Coins)
These cryptocurrencies comprise in-built features which make transaction details and user identities tough to trace:
Monero (XMR) provides a crucial advantage of comprehensive transaction privacy through its default features that include – Ring Signatures, Stealth Addresses and Ring Confidential Transactions (RingCT) – in order to conceal sender and receiver information and transaction amounts.
Zcash (ZEC) provides users with a comprehend sive option of usage of Zero-Knowledge Proofs (zk-SNARKs) to attain privacy, which allows them to make an informed choice between transparent or shielded transactions.
Dash (DASH): The PrivateSend mixing service of Dash empowers users to combine transactions which makes tracing more problematic even though this feature is optional.
Privacy-Enhancing Technologies (PETs)
These tools and techniques tend to be useful in improving privacy in cryptocurrency transactions:
- Mixers/Tumblers: Services that pool funds from multiple users and redistribute them to break the direct link between sender and receiver. Examples include CoinJoin (used by Wasabi Wallet and Dash’s PrivateSend).
The verification process of transactions through Zero-Knowledge Proofs (ZKPs) reveals that a transaction took place without revealing any information about the sender or receiver or the transaction amount. Used by privacy coins like Zcash.
The system generates a new address for each transaction through Stealth Addresses to stop users from linking their transactions to a single recipient. Used by Monero and Zcash.
- Ring Signatures: Combine a user’s transaction with others to obscure the actual sender’s identity. Used by Monero.
The Lightning Network functions as a Bitcoin Layer 2 solution which enables off-chain transaction processing while using onion routing to direct payments through multiple nodes for improved privacy.
Operational Security Practices
- Avoid Centralized Exchanges (CEXs) for Privacy: CEXs often require Know Your Customer (KYC) verification, linking your identity to your crypto assets. After buying crypto consider using decentralized platforms (DEXs) or transferring crypto to a self-custody wallet.
- For long-term storage use hardware wallets and for privacy-focused storage use Wasabi or Samourai wallets which include mixing features.
- Avoid Address Reuse: Creating a new address for every transaction makes it a lot harder to link your activities.
- Mask Your IP Address: It’s ideal to utilise a dependable Virtual Private Network (VPN) or the Tor browser when one intends to access his/her wallets or conducting transactions, especially on public Wi-Fi.
What’s important to be considered?
The methods enhance privacy but achieving complete anonymity proves difficult because blockchain systems operate with transparent operations.
The government and regulatory bodies are now paying close attention to privacy coins and mixing services because of their potential use in illegal activities. Some exchanges have even delisted privacy coins under regulatory pressure.
Users need to find equilibrium between their privacy requirements and regulatory requirements and the possible trade-offs of using specific tools which may result in reduced market liquidity and increased regulatory attention.
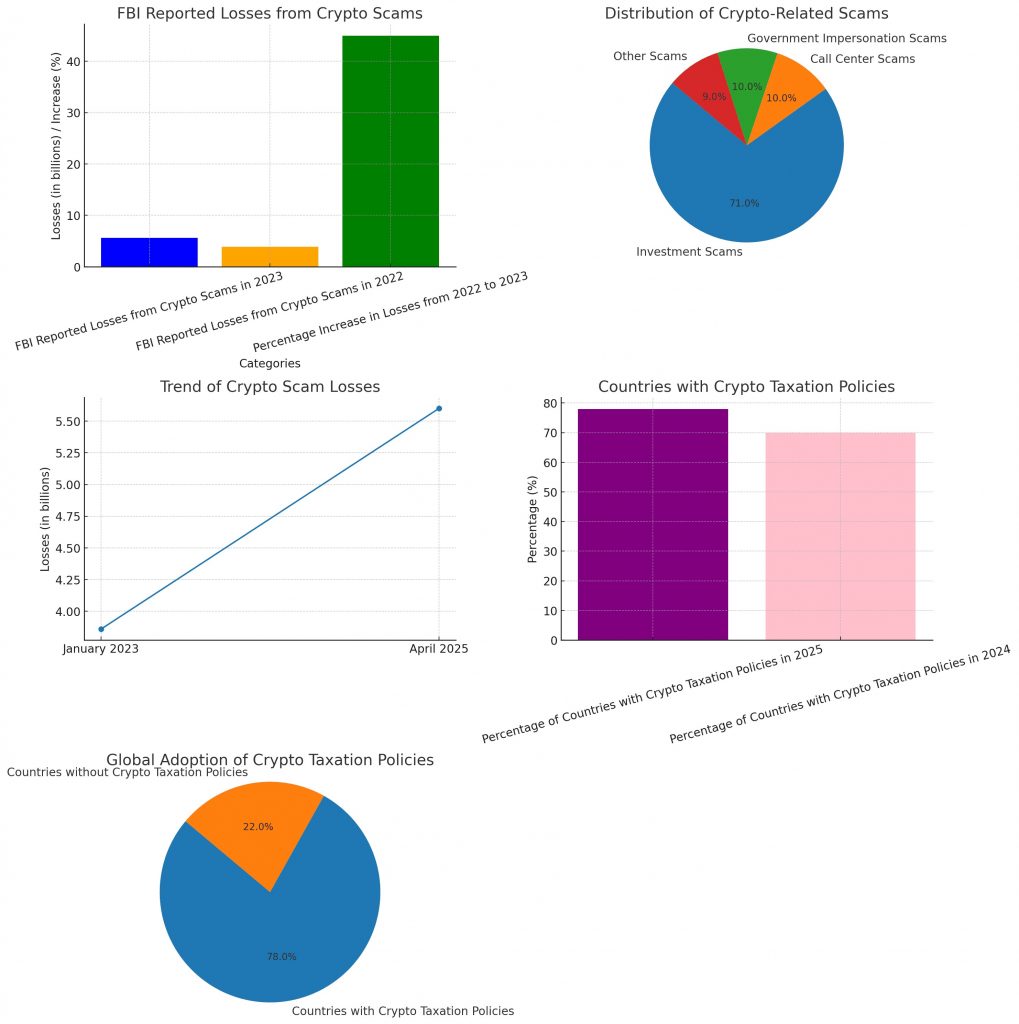
The charts depict data related to cryptocurrency scams and taxation policies. 1. The FBI reported losses from crypto scams for 2022 and 2023 through the first bar chart which shows a 45% increase in losses from the previous year. 2. The pie chart displays the types of scams, highlighting that investment scams account for 71% of total losses. 3.The line chart shows an increasing pattern of reported losses from January 2023 to April 2025 which indicates growing crypto-related fraud issues. 4. The second bar chart shows the percentage of countries that implemented crypto taxation policies in 2024 and 2025, which increased from 70% to 78%. 5.The pie chart shows that 78% of countries have implemented cryptocurrency taxation measures worldwide.
Best Ways to Keep Crypto Transactions Private
Here are some ways to enhance the privacy of your cryptocurrency transactions:
- Using privacy-focused cryptocurrencies
The privacy coins contain built-in features that make it impossible to see the sender, receiver and the amount of the transaction.
Widespread specimens include: The Monero (XMR), Zcash (ZEC) Firo (FIRO) and DASH (DASH).
- Using crypto mixers
The process of Crypto mixers involves collecting funds from various users before scattering them randomly which makes it hard to identify where the money started and where it ended up.
The mixing process exists in two forms: centralized which demands trust in a third party or decentralized through CoinJoin protocols for collaborative mixing.
The Mudrex Learn platform explains that advanced mixers achieve anonymity through three methods: fund splitting, transaction mixing and encryption techniques.
3.Utilizing off-chain solutions
The main blockchain does not handle off-chain transactions which enables users to maintain privacy while paying reduced fees.
- These transactions can involve payment channels or layer-2 solutions built on top of the main blockchain.
- The privacy solution mixnets operates off-chain to hide both network-level information including IP addresses and metadata.
- Employing Zero-Knowledge Proofs (ZKPs)
Zero-Knowledge Proofs (ZKPs) works as a cryptographic system; it enables verification of information without exposing its essential content.
The system enables users to verify transaction authenticity while keeping sender and receiver information along with transaction amounts completely hidden.
Hiro Systems explains that zk-SNARKs and zk-STARKs are two types of ZKPs used in blockchain applications to enhance privacy and scalability.
5.Choosing privacy-focused wallets and practices
Select wallets that protect privacy through features including:
Wasabi Wallet, Samourai Wallet, or Monero’s official wallet.
- The use of one address for various transactions enables authorities to track your activities more efficiently.
- You should use a VPN or Tor network to send transactions because it will hide your IP address.
- Select strong unique passwords for all your accounts during activation and activate two-factor authentication (2FA) for every account.
- Users should be cautious when dealing with suspicious emails and websites as phishing and scams are rampant and common in the crypto space.
Large cryptocurrency quantities are required to be stored in hardware wallets (cold storage) as this method reduces the chance of online theft.
The application of privacy-enhancing techniques, does not, always provide the advantage of complete anonymity in crypto transactions because certain methods create regulatory menaces. Research the particular features of privacy tools and their legal implications and risks before using them.
Tips to Stay Anonymous While Using Crypto
Tips to stay anonymous while using crypto
The majority of cryptocurrencies maintain pseudonymity instead of complete anonymity in their operations
The system connects transactions to wallet addresses instead of personal identities, but analysis of patterns could reveal user identities.



To enhance your anonymity when using cryptocurrency:
- New address should be created for every transaction to prevent your activities from tracking.
- Specific wallets should be chosen, which will automatically generate addresses and support CoinJoin (transaction mixing) and Tor like Wasabi Wallet or Samourai Wallet.
- Privacy Coins need to be used as a solution by implementing cryptocurrencies that provide better anonymity features that include Monero (XMR) with ring signatures and stealth addresses and Zcash (ZEC) with zk-SNARKs privacy option.
- One can Mask IP Address – Ensure you employ VPNs (Virtual Private Networks) or Tor to obscure your IP address and location when making transactions.
- Mixers/Tumblers Service can be considered; they combine transactions from multiple users that can disrupt or break the link between sender and receiver, but be aware of potential fees, legality, and trust required.
- Trade on P2P Platforms or Bitcoin ATMs: All of those allow for transactions with limited or no ID verification, specifically for smaller amounts, but check local regulations.
Key Considerations
- Blockchain Transparency: Most transactions tend to be recorded on a public ledger (blockchain), making them visible, even if identities aren’t initially attached.
- KYC Requirements: Centralized exchanges and such services necessitate identity verification (Know Your Customer) which links your identity to your wallet and transactions.
The legal status of mixing services remains uncertain because Tornado Cash and similar services have encountered regulatory challenges because of money laundering suspicions in various jurisdictions. The implementation of enhanced privacy measures could result in trade-offs that include reduced market liquidity and higher transaction fees and increased regulatory oversight.
Researching the risks and regulations of privacy tools and techniques you want to use is essential.
Conclusion
Generally speaking, the world of cryptocurrency is constantly changing, and so are the ways that governments try to keep track of it. Since there’s more and more attention from regulators, people who use digital assets need to understand that their transactions aren’t really private.
New blockchain forensics software and AI surveillance can help authorities find transaction patterns and connect wallet addresses to actual people. Non-custodial wallets together with privacy coins provide anonymity but they do not offer complete protection.
The Bloomberg article shows that governments now monitor cryptocurrency activities more intensely to enforce rule compliance and transparency requirements. The new Income Tax Bill in India shows how governments are increasing their oversight of crypto activities by requiring people to follow rules and disclose their activities.
The complete invisibility in the crypto world during 2025 seems unlikely but you can still use good practices to handle these challenges.
To regain control of your financial privacy you must stay informed while using smart strategies that help you stay careful and avoid easy surveillance.
References:
- Arnaldo Jorge Acevedo. ‘Government Influence in Cryptocurrency: Exploring Allegations of NSA Involvement in XRP Creation.’ Arnaldo Jorge, 4/9/2024
- Andrew Bush. ‘Jewish Studies.’ A Theoretical Introduction, Rutgers University Press, 3/8/2011
- Link1
- Link2
- Link3
Image References:
- Image: Overview of India’s New Income Tax Bill and Financial Surveillance Measures, Accessed: 2025. https://preview.redd.it/indias-new-tax-bill-privacy-is-dead-v0-yaks43bmg6re1.png?width=640&crop=smart&auto=webp&s=d66f94d73129c105f2e713257b24b79d03da753f
You need to login in order to Like




















Leave a comment