Overview of Fake Phone Crypto Scams
Smartphone adoption for financial management has led to sophisticated scams targeting crypto users who remain unaware of these schemes. Fake phones have emerged as a major security threat which targets crypto users. The devices used in these scams include counterfeit products and infected used phones and modified genuine phones with dangerous software. The attackers use these compromised devices to obtain private keys and seed phrases which enable them to steal cryptocurrency directly from users’ accounts. The attackers succeed in their operations because the malware maintains its presence on infected systems.
Warning Signs of Counterfeit Phone Crypto Scam
The application enables attackers to create hidden entry points and control clipboard content and deploy counterfeit wallet applications that duplicate authentic wallet interfaces. Users need to watch for suspicious indicators of fake phones because these devices often arrive with unauthorized applications and experience rapid battery depletion.
Users who verify information through trusted sources and implement robust security measures will minimize their exposure to fake phone crypto scams while making informed decisions protects their investments.
Common Attack Vectors Used by Hackers
The rise of counterfeit phones which threatens cryptocurrency security demonstrates that cybercriminals choose established attack methods because they generate financial gains. The counterfeit devices contain hidden backdoors and trojans which enable hackers to establish permanent access to your phone system for complete data extraction. The current malicious technique known as clipboard hijacking has become popular among attackers.
The malware operates by hiding behind your clipboard to replace your crypto wallet address with the attacker’s address without your knowledge. Your funds will be redirected to an unknown destination without any warning to you. The identity theft attack against twenty Israeli crypto industry leaders became a major news story. [cited]
Such attacks produce major problems for all people who experience them. Users need to stay vigilant and use robust security measures because these advanced security threats require constant attention. Your digital assets receive protection in an escalating dangerous online world through understanding attack vectors which serve as your primary defense mechanism.
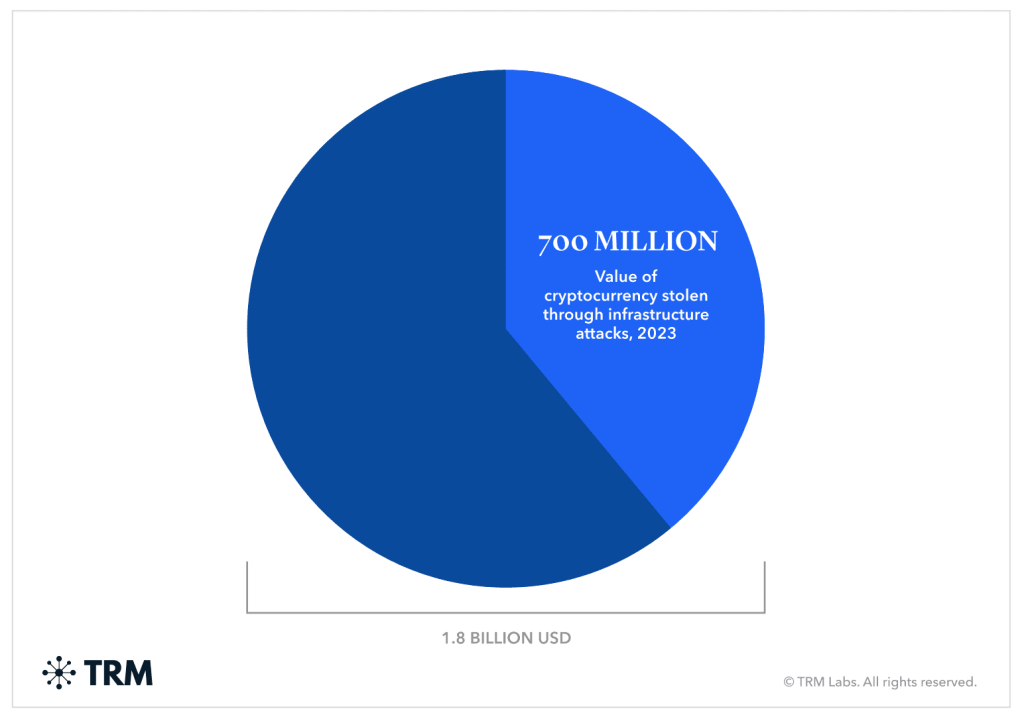
A single image contains more value than a thousand words according to common belief. The graphic demonstrates the extent of cryptocurrency theft through infrastructure attacks which proves why we must address these threats with urgency.
| Attack Vector | Prevalence |
| Phishing | 35% of cyber-attacks during the COVID-19 pandemic |
| Email Attachments | 92% of malware delivered via email |
| Social Engineering | 50% of security breaches involved social engineering in 2023 |
| Ransomware | 24% of security breaches involved ransomware in 2023 |
| Insider Threats | 83% of breaches involved external actors in 2023 |
Common Cyberattack Vectors and Their Prevalence
Technical Mechanisms of Address Swapping and Seed Phrase Capture
How Fake Phones Swap Crypto Wallet Addresses
The methods hackers employ to steal cryptocurrency through fake devices have evolved into sophisticated combinations of social engineering tactics and advanced technical methods. Address swapping represents one of the most deceptive methods hackers use to steal cryptocurrency.
The malware on compromised phones detects when users copy their crypto wallet addresses. The attacker gains control of the transaction by modifying the original address to one of their own.
The modification of URI handling enables malicious applications to intercept and modify deep links which users use for transactions. The combination of clipboard sniffers and overlay attacks enables hackers to steal private information while displaying deceptive interfaces which make users unknowingly validate altered addresses.
The integration of keyloggers with fake user interfaces allows attackers to simultaneously steal seed phrases which enhances their ability to conduct attacks. The advanced methods used by cybercriminals prove their technical abilities while showing why crypto users must protect their devices and transaction methods.
How Fake Phones Capture Crypto Seed Phrases
The use of fake phones which include counterfeit or inexpensive Android devices obtained from unofficial sources creates a major threat to cryptocurrency users because these devices frequently contain malware that steals seed phrases. The embedded malware in these devices runs at operating system and firmware levels which makes complete removal through factory resets or antivirus software programs nearly impossible.
Here’s how seed phrases are captured:
The Triada Trojan along with other pre-installed malware exists in counterfeit phones to steal cryptocurrency through wallet address swapping and 2FA message interception and private key access. The malware operates in stealth mode to extract user credentials and sensitive information while remaining undetectable to users.
The distribution of malicious apps through unofficial app stores and compromised frameworks and fake links leads users to install apps that pretend to be crypto wallets or useful tools.
These installed applications perform three main functions:
The applications use phishing tactics to make users reveal their seed phrase through fake login interfaces and wallet recovery simulations.
The malware uses Optical Character Recognition (OCR) to extract seed phrases from images stored in the gallery while also stealing device screenshots and photos.
The seed phrase becomes visible to attackers through keylogging which records all entered keystrokes.
The clipboard hijacking feature allows attackers to replace copied wallet addresses with their own controlled addresses.
Scammers use fake wallet recovery services to trick users into giving away their seed phrase which they then use to steal cryptocurrency funds.
The attackers gain access to wallets through pre-seeded hardware devices because these devices include seed phrases that they already possess.
- Users can protect themselves from pre-installed malware by buying their phones from authorized manufacturers and reputable retailers. The following is a list of the steps that can be taken to prevent hardware attacks.
- Buying Devices from Reliable Sources: Users who buy phones from authorized manufacturers and reputable retailers can prevent pre-installed malware from being installed on their devices.
Hardware Bouts
- Seed phrases should never be stored digitally through screenshots or notes or cloud storage because this method is wallets function as offline storage solutions for long-term cryptocurrency assets because they add an extra security barrier against device insecure. The recommended method involves writing down seed phrases and storing them in an offline secure location.
- Users must check the official app stores for wallet applications and verify the publisher before installation while being alert to suspicious messages and links that could lead to seed phrase entry on fake websites.
- Two-factor authentication (2FA) should be enabled for all financial and crypto accounts while using application-based authentication instead of SMS-based verification. [Link1]
Triada Trojan Fake Phone Crypto Attack Explained
The Triada Trojan has undergone major development because researchers discovered its latest version embedded in counterfeit Android smartphones that vendors sell through online channels.
The advanced malware creates a severe security risk which primarily targets users who store cryptocurrency assets.
The Triada Trojan establishes itself at the firmware level of devices before users acquire their phones which makes complete removal impossible through factory resets or antivirus software.
The malware operates through two methods to steal cryptocurrency funds.
The malware system tracks clipboard operations and cryptocurrency application transactions to swap wallet addresses with attacker-controlled addresses during fund transfers.
The malware system has the ability to swap genuine QR codes in applications with fake ones which redirect users to attacker-controlled wallets.
Kaspersky researchers discovered that this version of Triada has stolen more than $264,000 worth of cryptocurrency from 2,600 users across Russia and four other countries since June 2024.
The Triada malware system performs cryptocurrency theft operations but it also carries out additional malicious activities.
- The malware steals login information and session cookies from users who use WhatsApp and Telegram and TikTok and Instagram.
- The malware system intercepts SMS messages which include two-factor authentication (2FA) verification codes.
- The malware system takes control of user communications by sending messages and deleting them from the user’s account.
- The malware system tracks user browser activities while redirecting users to dangerous websites.
Recommendations for Protection
- Buy your mobile devices from authorized retailers because unauthorized online stores and counterfeit products should be avoided.
- Security software from Kaspersky for Android can detect infections although complete removal remains challenging.
- Users who detect Triada on their devices should perform a device reflashing operation either by using official firmware or by seeking assistance from experts.
- Users should examine their social media and messaging accounts for suspicious activity while ending unauthorized sessions and performing regular password updates.
- Users should handle all downloaded applications with caution by avoiding unknown sources and treating all links and attachments with suspicion while maintaining their operating system and application software up to date. [Link2]
How to Avoid Fake Phone with Crypto Malware
Here’s how to prevent crypto malware on phones
The following steps will help you prevent fake phones with crypto malware from infecting your devices:
- Buy your phones from authorized dealers who represent official manufacturers. It is not safe to purchase used phones from unverified sellers at auction sites because these devices could contain malware.
- Your operating system and security software require immediate updates to defend against malware attacks that target system vulnerabilities.
- Users must obtain their apps only through official stores Apple App Store and Google Play Store and verified developer websites.
- Before installing any cryptocurrency wallet you should verify the publisher details displayed on the screen.
- Crypto malware detection requires users to watch out for specific warning indicators on their mobile devices.
What to do if you suspect infection?
Take these actions when you suspect your device has been infected.
- Disable your internet access by turning off Wi-Fi and mobile data right away.
- Run a security scan using a trusted antivirus application.
- The user should delete all untrusted applications which the scan detects or which appear suspicious.
- A factory reset should be your final option to eliminate malware but first save all your important data.
A few security tips to protect your phone:
- The first set of security measures should be their operating system and apps through regular software updates to maintain system security.
- Users should download all applications through followed by regular maintenance practices to maintain phone security.
The following steps should be taken:
- Users should update official app stores.
- Users should activate built-in security options which include screen locks and biometric authentication and remote wipe functionality.
- The installation of trustworthy anti-malware protection software should be your priority.
- Users should handle links and attachments from unfamiliar senders with extreme caution.
- Users need to use public Wi-Fi with caution by enabling VPN protection for secure network access.
- Users need to review their app permissions while restricting access to particular applications.
- Users need to stay aware of active security threats that exist in the present.
- Users should activate two-factor authentication (2FA) for their crypto and financial accounts.
- Users should store their cryptocurrencies in hardware wallets because they offer better protection than software wallets.
- Users should track their crypto wallet transactions to detect any abnormal activity.
- The developer options should remain disabled unless you need to use them. [Link3]
Conclusion
The cryptocurrency sector remains vulnerable to security threats because hackers can easily compromise phones through fake or tampered devices. The presence of malicious software in these phones enables hackers to access sensitive information which makes cryptocurrency theft operations straightforward.
The increasing number of security incidents including the $700 million infrastructure attack in 2023 [cited] demonstrates the critical need for this protection. Users who understand the methods behind attacks such as clipboard hijacking and fake wallet applications can better recognize potential dangers.
The key to protection lies in taking proactive measures. Users must remain vigilant by verifying their devices’ authenticity while implementing robust security protocols.
Users who combine hardware wallets with transaction monitoring systems achieve better protection against wallet address mistakes and seed phrase thefts. Your digital assets need immediate protection because the present technological environment continues to create security threats for your cryptocurrencies.
References:
- ‘AN1MAGINE.’ Volume 9 Number 1 January-March 2025, An1mage, 3/31/2025
- Jason Scharfman. ‘The Cryptocurrency and Digital Asset Fraud Casebook, Volume III.’ Exchange Hacks, Deepfakes, Social Media, and Artificial Intelligence Scams, Springer Nature, 5/26/2025
- Link1
- Link2
- Link3
Image References:
- Image: Value of cryptocurrency stolen through infrastructure attacks in 2023., Accessed: 2025. https://cdn.prod.website-files.com/6082dc5b670562507b3587b4/68a4b55db8fdb93217c5728b_Screenshot%202025-08-19%20at%201.33.08%E2%80%AFPM.png
You need to login in order to Like



















Leave a comment