Crypto Security and Its Importance
Digital transformation has created financial opportunities through cryptocurrencies, yet these digital assets present significant security risks to users. The first requirement for users who want to succeed in this complex financial system involves understanding fundamental crypto security principles.
Major financial losses from cybercriminals have become more dangerous because they now employ advanced phishing methods and deceptive scams. People now handle their financial transactions independently so they must take full responsibility for safeguarding their investments.
Every investor who wants to protect their assets needs to understand the fundamental principles of crypto security regardless of their experience level. A solid defense against evolving threats requires investors to implement security measures which include two-factor authentication and secure wallet practices and scam avoidance.
The image [cited] demonstrates how different digital security elements connect to each other which proves that users need complete protection strategies for their cryptocurrency assets in this dangerous digital environment.
How to Avoid Crypto Scams: Strategies to Avoid Crypto Scams
The evolving nature of cryptocurrencies leads to more complex scams which require users to take additional precautions for their digital wallet security. Before taking any action verify the website address because fake websites use advanced techniques to impersonate legitimate exchanges.
Investment opportunities require thorough examination because social media and unverified platforms often promote scams that seem too attractive to be real. Researching project teams and reviewing their token contracts through CoinMarketCap will provide essential protection.
The cybercrime department needs reports about suspicious activities to protect all users within the crypto community. The visual aid in demonstrates how different security elements connect to each other which proves that multiple protective measures must be implemented to prevent scams.
| Year | Total Losses (USD) | Percentage Increase from 2022 | Most Affected Age Group | Percentage of Total Losses from Investment Scams |
| 2023 | Over $5.6 billion | 45% | 40-49 years | 71% |
Reported Losses to Cryptocurrency Investment Scams (2023)
How to Protect Cryptocurrency from Hackers: Best Practices for Protecting Cryptocurrency from Hackers
Cryptocurrency investors need to create strong security systems because digital threats in cyberspace continue to rise. All exchange accounts require two-factor authentication (2FA) as an essential security practice.
The implementation of two-factor authentication (2FA) or multi-factor authentication (MFA) [provides] additional security layers which protect crypto exchange accounts from unauthorized hacker access.
Two-factor authentication (2FA) requires users to verify their identity through two different methods beyond password entry which effectively reduces cybercriminal access to user accounts even when passwords become exposed.
Users should implement hardware wallets as their storage solution because these devices function as cold storage systems. The storage system protects assets by keeping them offline from cyber attackers who want to access them.
Security software updates combined with transaction avoidance on public Wi-Fi networks enhance the existing security measures. The implementation of these security practices leads to two main benefits: it decreases overall risks and creates an environment where cryptocurrency operations become more resistant to threats.
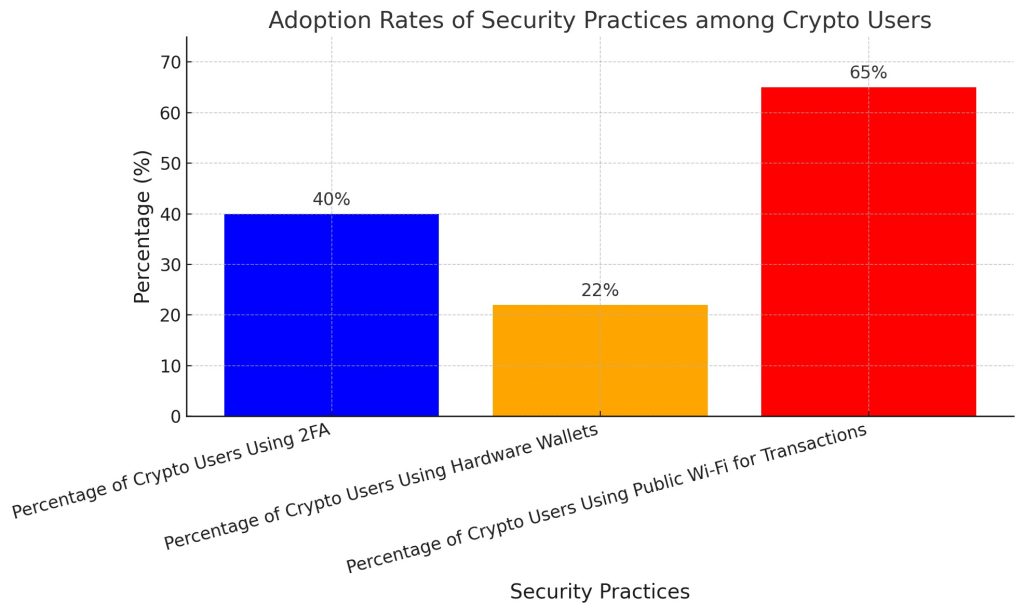
The bar chart demonstrates how cryptocurrency users adopt different security practices through their adoption rates. The data reveals that 40% of users activate two-factor authentication (2FA) while 22% choose hardware wallets and 65% perform their transactions through public Wi-Fi networks. The security measures need improvement because users show low interest in 2FA and hardware wallets, yet they frequently use public Wi-Fi which creates a major security threat because of its exposed nature to cyber-attacks.
How to Avoid Crypto Scams and Phishing Attacks?
Phishing attacks represent the primary method which crypto scammers use to target their victims. Users become victims of wallet credential theft through deceptive websites and deceptive messages which attackers use to obtain their wallet information.
How to Stay Safe:
- Users should save official exchange websites in their browser bookmarks.
- Users should never follow links which appear in direct messages or unrequested emails.
- Users should verify the authenticity of official Twitter and Discord channels.
- Brave stands as a phishing-resistant browser which users can use for protection.
- Users should activate anti-malware extensions together with crypto phishing detection tools.
Mistakes to Avoid When Storing Cryptocurrency
The most experienced traders continue to make security mistakes which they should avoid
Common Mistakes:
- Users store their seed phrases through screenshots and cloud storage platforms.
- Users reveal their wallet QR codes to the public.
- Users neglect to create wallet backups before performing software updates.
- Users should never disregard warning signs about unauthorized wallet access in DeFi applications.
- Always remember: “Not your keys, not your coins.”
Best Practices for Crypto Wallet Security
Your digital vault exists as a wallet which requires proper protection. You should handle your wallet with the same care as you would your physical safe.
Wallet Security Checklist:
- Users should select their wallets from established providers which include Ledger and Trezor and MetaMask.
- Users should store their private keys in physical paper format or encrypted USB drives for backup purposes.
- Users should disable their browser extensions whenever they access their hot wallets.
- Users must check the authenticity of wallets before downloading them because multiple fake applications exist in app stores.
- Your wallet remains at risk of vulnerability whenever it operates continuously throughout the day.
Why DYOR Is Important in Crypto?
The crypto investment principle of DYOR (Do Your Own Research) stands as the most essential rule. The decentralized blockchain system requires you to handle both banking and risk management responsibilities independently.
Why It Matters:
- Investors need to perform their own research before they choose to follow influencers or hype tokens.
- Investors need to evaluate their investments by looking at actual market results while also verifying both market liquidity and developer reliability.
- Investors who practice DYOR gain understanding about tokenomics and project development plans and security audit results.
DYOR Tools:
- Glassnode provides users with blockchain analytical data.
- Users can access DeFi rankings through DefiLlama.
- Users can verify project legitimacy through CoinMarketCap.
- The lack of knowledge about crypto investments leads to costly financial losses.
Crypto Security Measures and Rules
The following basic crypto security rules must be followed to achieve uniform protection of assets.
- You must never disclose your private keys or seed phrases to anyone including customer support staff.
- Hardware wallets serve as the best option for protecting your assets when you need to store them for extended periods.
- Spread your investments across different platforms because storing all coins on one exchange creates security risks.
- Check exchange security policies and system updates on a regular basis.
- Check your transaction records for any unusual activities.
- Your funds will stay protected through these practices because they create multiple security layers that protect your assets when one fails.
Hardware Wallet vs Software Wallet Crypto Safety
The decision between hardware wallets and software wallets for crypto storage depends on whether users want security or convenience.
| Feature | Hardware Wallet | Software Wallet |
| Connectivity | Offline (cold storage) | Online (hot storage) |
| Security Level | High | Moderate |
| Accessibility | Limited but safer | Instant, riskier |
| Ideal For | Long-term storage | Daily transactions |
Verdict:
Users should store their long-term savings in hardware wallets such as Ledger Nano X or Trezor but should use software wallets including MetaMask or Trust Wallet for their fast-trading operations.
Best Cold Storage Strategies for Cryptocurrency
The most secure way to store cryptocurrency requires users to keep their assets offline by using cold storage solutions.
Top Cold Storage Strategies:
- Users should store their assets on air-gapped devices because these devices operate without any internet connection.
- Users should place their hardware wallets inside safe deposit boxes or fireproof safes for maximum security.
- Users should protect their private keys through Shamir’s Secret Sharing or multi-sig setup methods.
- Users should distribute their backup copies across different locations throughout the world.
- Users can establish a “crypto inheritance plan” which grants secure access to their assets for their designated heirs.
How to Create a Strong Crypto Wallet Password
- A strong crypto wallet password requires specific steps for its creation.
- Your password functions as your main security protection. Make it unbreakable.
Password Tips:
- The password needs to contain both uppercase letters and lowercase letters and numbers and special symbols.
- The password needs to contain at least 16 characters for maximum security.\
- Stay away from using words found in dictionaries and dates from your birth.
- Users should implement password management through Bitwarden or 1Password.
- Users should update their passwords whenever platform security incidents occur.
A hacker using brute-force methods can break an 8-character password within minutes but a 16-character randomly generated string becomes virtually unbreakable for centuries.
Protecting Crypto on Exchanges Tips
- Exchanges provide users with easy access but their systems lack the security features needed for permanent asset storage.
- Exchanges require users to follow these safety measures:
- Users must activate two-factor authentication and anti-phishing protection codes for their accounts.
- Users should remove their trading funds from the exchange platform right after completing their trades.
- Users should select exchanges which demonstrate strong audit transparency in their operations.
- Users should maintain only essential funds within custodial exchange platforms.
- Users should select exchanges which demonstrate proof-of-reserve verification through Binance and Kraken and Coinbase.
- The theft of more than $2 billion worth of crypto assets from centralized exchanges during 2018-2024 demonstrates why users need to control their assets through self-custody.
Crypto Seed Phrase Safety Guide
Your seed phrase which consists of 12 to 24 words functions as the primary access key to your wallet because anyone who possesses it gains control over your digital assets.
Seed Phrase Safety Guidelines Include the Following:
- The seed phrase should be written by hand on paper or metal instead of digital storage.
- Maintain different secure locations for storing your backup copies.
- Never send your seed phrase through email or take its picture.
- Metal backup plates serve as durable storage solutions for extended periods.
- Check your backup storage accessibility at regular intervals.
- The loss of your seed phrase becomes permanent so you must handle it with absolute care.
Conclusion
Digital security of cryptocurrency assets has become essential because of the rapid pace of modern digital technology. People who gain financial independence through investing need to protect their assets because scams and cyber threats have become widespread.
The protection of your assets depends on implementing three essential security methods which include cold wallet storage and robust security systems and complete awareness about phishing schemes. The visual security measures [cited] provide investors with multiple strategies to minimize their digital investment risks.
The security protocol system provides multi-level protection while demonstrating that individual user attention remains essential for complete security. The secure management of cryptocurrency requires investors to stay informed about new threats while taking active measures to protect themselves in the complex cryptocurrency market.
![]()
Image1. Digital security concepts represented through neon icons.
References:
- Zach Abraham. ‘Bitcoin and Crypto Scams.’ How to Avoid Bitcoin and Cryptocurrency Scams, Amazon Digital Services LLC – Kdp, 12/25/2018
- R. Aruna. ‘Cryptography and Cyber Security.’ Dr. Sanjay H S, RK Publication, 2/24/2025
Image References:
- Image: Digital security concepts represented through neon icons., Accessed: 2025. https://cdn.prod.website-files.com/660a94378d5efa3a1040a763/682d9eed0845695d39de48da_6819e9664941d5e7ca88f632_Best%2520practices%2520to%2520keep%2520your%2520crypto%2520safe.png
You need to login in order to Like



















Leave a comment